| Lesson 2 | What is a role? |
| Objective | Understand how database roles are used |
How Database Roles are used
A role [1] is a way to group a series of security privileges[2] into a single entity. You can then use the role as a management tool for assigning and changing security privileges for individual users that are assigned the role. A role is an intermediary between individual object grants and individual users. You assign a set of privileges to a role, and then assign users to that role.
Group Security Privileges
Oracle roles are a powerful and efficient method for managing security privileges in an Oracle Database. They provide a centralized approach to granting and maintaining access rights for users by grouping a series of security privileges together. By using roles, administrators can simplify the task of managing access control, enhance security, and promote consistency across the database environment.
The following points highlight the key aspects of Oracle roles in relation to the grouping of security privileges:
Oracle roles offer a streamlined and scalable approach to managing security privileges in an Oracle Database. By grouping related privileges together and utilizing role-based access control, administrators can simplify access management, enhance security, and improve maintainability across the database environment.
- Role-based Access Control: Oracle roles follow the Role-Based Access Control (RBAC) model, which assigns access rights and permissions based on roles rather than individual users. This model allows for a more manageable and scalable approach to security administration, especially in large and complex database environments.
- Privilege Consolidation: Oracle roles consolidate multiple security privileges, including object and system privileges, into a single entity. This enables administrators to grant or revoke a set of related privileges to users with a single command, simplifying the process of managing access rights.
- Hierarchical Structure: Oracle roles can be hierarchical, meaning that roles can be granted to other roles, forming a nested structure. This allows for the creation of a multi-level access control hierarchy, making it easier to manage privileges for groups of users with similar responsibilities and access requirements.
- Flexibility: Oracle roles offer flexibility in terms of privilege management. Roles can be created to suit specific organizational requirements, such as job functions, departments, or projects. This allows for a tailored approach to access control, ensuring that users only have the necessary privileges to perform their duties.
- Dynamic Role Assignment: Oracle roles can be assigned to users either statically or dynamically. Static role assignment involves granting a role directly to a user, while dynamic role assignment occurs through the use of PL/SQL packages or procedures. Dynamic role assignment provides greater control over access rights, as roles can be assigned or revoked based on specific conditions or events.
- Maintainability: Oracle roles simplify the process of updating security privileges. When a new privilege needs to be added or an existing privilege modified, administrators can make the change at the role level, which automatically propagates to all users assigned to that role. This eliminates the need to modify privileges individually for each user.
- Auditing and Monitoring: Oracle roles facilitate auditing and monitoring by providing a clear and structured view of access rights within the database. By analyzing the roles and their associated privileges, administrators can quickly identify potential security vulnerabilities or areas of excessive access.
Oracle roles offer a streamlined and scalable approach to managing security privileges in an Oracle Database. By grouping related privileges together and utilizing role-based access control, administrators can simplify access management, enhance security, and improve maintainability across the database environment.
Advantages of roles
You can use roles to simplify security administration and implementation in four ways:| Simplified granting of privileges: | By grouping privileges into a role, you reduce the amount of effort needed to grant multiple privileges. |
| Simplified management of privileges: | To change the object privileges for a group of users assigned to a role, you can change the privileges for the role instead of the privilegesfor each individual user |
| Dynamically changing security privileges: | A user can assume more than one role, and can change roles while connected to the database. You can enable and disable roles as an administrator. |
| Application roles: | You can create application roles, which allow all users of an application to have the same privileges while using the application. |
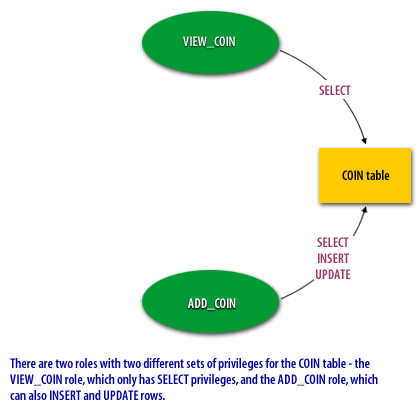
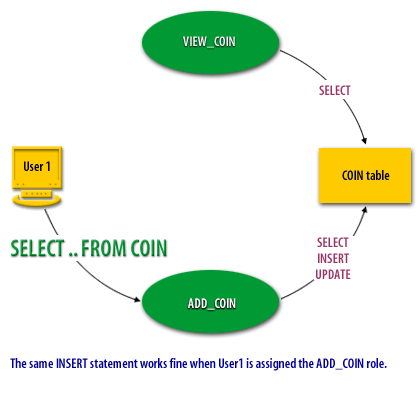
- There are 2 roles with 2 different set of privileges for the COIN table, the VIEW_COIN role, which only has SELECT privileges, and the ADD_COIN role, which can also INSERT and UPDATE rows
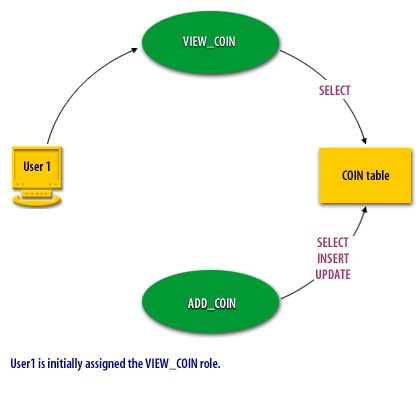
- User1 is initially assigned the VIEW_COIN role
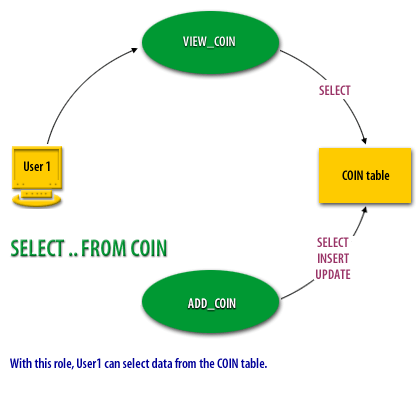
- With this role, User1 can select data from the COIN table
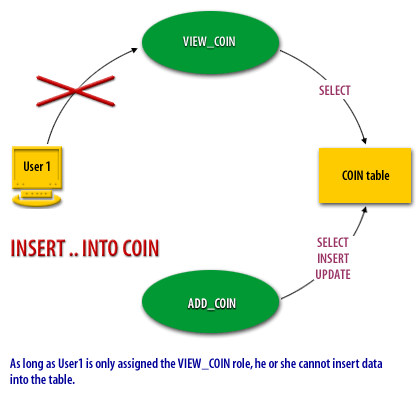
- As long as User1 is only assigned the VIEW_COIN role, he or she cannot insert data into the table
- The same INSERT statement works fine when User 1 is assigned the ADD_COIN role
The next lesson shows how to create a role.
[1]Role: A collection of privileges that can be assigned together.
[2]Privilege: The capability to perform some type of database action.